
Abstract vector created by fullvector - www.freepik.com
One of the main themes that will be highlighted at WATEC 2017 is “Securing our Future: Water Industry Embracing Cyber Technologies.” In this blog, we will explore what this means and why it has become such a hot topic in the water industry.
A few words on cyber-crime
Two massive ransomware attacks have dominated the news this year — WannaCry and, most recently, Petya. Hospitals and other healthcare facilities in Britain were affected, as were major corporations such as banks, shipping companies and advertising agencies.
Ransomware is just one example of malicious criminal activity in cyber space, known collectively as cybercrime. Whether for profit, activism (“hactivism”), or espionage, cybercrime includes activities such as phishing emails (that steal credit card numbers and other personal financial information), zero day attacks (that exploit application security vulnerabilities before they’re discovered), and rootkits (that enable unauthorized access to a computer system at the root or admin level). [2]
In all its forms, cyber-crime is expected to cost its victims – which include you and me – as much as $6 trillion by 2021. [1]
Digital transformation has created cyber-physical systems
As shown in the concept map below, the convergence of sensors, IP networks, processors, actuators and informatics has transformed what used to be purely physical systems, such as buildings and vehicles, into cyber-physical systems that sense and interact with the physical world. Advances in machine learning, artificial intelligence and predictive analytics are making these cyber-physical systems increasingly smart and autonomous, with unprecedented levels of performance and efficiency.
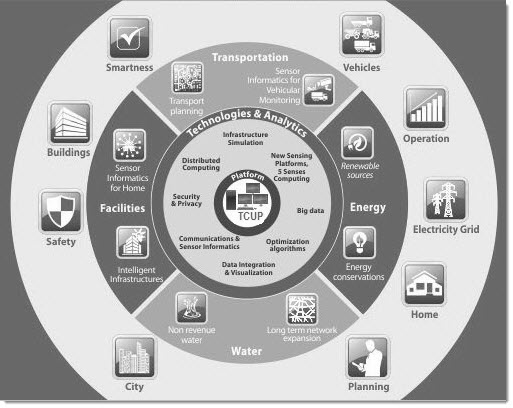
This trend is having a deep impact on water distribution systems as well. To solve water scarcity problems and to meet regulator demands for greater efficiency, water utility operators are adopting digital technologies and big data to improve leak detection, optimize infrastructure planning, reduce maintenance costs, and enhance customer service. The pace of adoption is often dictated by the urgency of the need, with water-scarce countries such as Australia and Israel being among the fore-runners in developing and adopting digital tools. [3]
The Security Risk and How to Mitigate It
The emergence of cyber-physical systems holds great promise for improving the quality of many aspects of our lives, but it also introduces the risk of increased exposure to cybercrime. Already in the late 1990’s the US President’s Commission on Critical Infrastructure Protection (CCIP) identified eight infrastructure systems, including water supply systems, that play a critical role in the fabric of modern society. If any one of these systems were to be brought down by a successful cyber attack, the impact on the economy and on daily life in general would be catastrophic. [4]
The US Homeland Security Department, and other governments around the world, are actively partnering with academia, industry, entrepreneurs and investors to advance interoperable, high-quality security solutions that can be deployed across cutting-edge infrastructures to secure the control systems — and the data they rely on — from cyber attacks. [5]
When it comes to water utilities, the following are some ways to mitigate the risk of a cyber attack [1]:
- Build robust models for detecting and rapidly dealing with cyber attacks.
One attack and defense model that has been proposed, for example, is the RAIM model [6], based on Real-time Monitoring for rapid Anomaly Detection and robust Impact Analysis and Mitigation Strategies. - Segregate control systems so that a breach will not create a domino effect across all essential functions.
- Choose solutions that are secure by design.
- Hire personnel who specialize in the field.
More and more water utilities are establishing positions such as Chief Data Officer or Information Security Officer, whose job it is to help prepare, prevent, detect and respond effectively to ever-changing cyber threats. - Most cyber attacks are the result of human error, such as falling prey to phishing emails. All personnel in the facility need to be educated on the dangers of cyber threats and how to avoid them.
References
[1] Key to ensuring cyber security now and into future, Australian Water Association, June 30, 2017
[2] Department of Homeland Security, Cyber Security Division
[3] Frank Cespedes and Amir Peleg, How the Water Industry Learned to Embrace Data, Harvard Business Review, March 27, 2017
[4] Performance, Robustness, and Cyber Security of Critical Infrastructure Systems – A Cyber-Physical Systems Research Theme
[5] Dr. Robert Griffin, Securing Critical Infrastructure in the 21st Century, Department of Homeland Security Science and Technology (S&T) Directorate, March 20, 2017
[6] C. Ten et al, Cybersecurity for Critical Infrastructures: Attack and Defense Modeling, IEEE Transactions, July 2010